Ahead of the Holidays, Card Scammers Target Booking Users

In mid-November, a new large-scale wave of phishing attacks emerged, targeting once again customers of the Booking.com service. These attacks pose the greatest threat just before major holidays, precisely when travel plans are in full swing with the approaching Christmas and New Year celebrations. The author also found themselves as a target of such an attack but thankfully avoided falling victim. The method chosen by scammers is highly perilous, not only allowing them to siphon money from cards but also acquire personal data about potential victims. So, it's crucial to stay vigilant: refrain from clicking on suspicious web addresses that may resemble the genuine ones but, in reality, are not.
If a traveller has managed to secure a hotel room or apartment well in advance and at a very low cost through a booking service, they should not be overly elated. This makes them an attractive target for scammers. Especially on the eve of festive holidays, when the threat of losing a coveted, cheap, and convenient accommodation (yes, it happens!) entices travellers to fall into the trap of fraud. The author of this article found themselves as a target of such scammers, and some knowledge about phishing prevented them from becoming a victim. A brief investigation revealed that this is not an isolated case, warranting a closer look into its causes.
How It Typically Happens
In the Booking.com service and other hotel and apartment booking platforms, there is a messaging system that allows travellers to communicate with the administration or property owners. Nothing criminal here; owners explain the contactless key retrieval process or inquire about the guest's possible arrival time. Travellers clarify important details or notify about additional needs. However, at some point, the future guest receives a message seemingly from the property owners, stating that their reservation will be canceled in a day if they don't provide additional information and confirm their payment card details.
Naturally, this causes some concern, as there is not much time left before the trip, reducing the chances of finding an alternative location. If a person is not too attentive, they might click on the link provided in the message received via Booking.com or another service. This opens a webpage that strikingly resembles the original payment confirmation page of the accommodation booking service. Simply entering the card details results in funds being withdrawn. For reference, there is a screenshot provided alongside this article, depicting such a panic-inducing message supposedly from property owners, inviting the recipient to click on a link to confirm card details. Upon closer inspection of the link, it becomes apparent that it mimics the web address of Booking.com but has no affiliation with the genuine service.
For instance, a well-known case involved a guest who had booked a room at the Amara Singapore hotel. An additional 9,000 Singapore dollars (equivalent to 6,150 euros) were fraudulently charged on top of the hotel payment after the guest received a phishing message through Booking.com's messaging center. The guest had booked a place for their 35th birthday celebration and made a full prepayment of 3,000 Singapore dollars through Booking.com. Subsequently, he received an email from the booking platform signed by a certain "Rosa Zukauskene," claiming to be a senior property manager at Amara Singapore. The email contained a phishing link through which the funds were stolen.
In the case the author encountered, a natural distrust of unfamiliar web links played a crucial role. Instead of following the scammers' script, the potential victim reached out to Booking.com support, receiving sound advice not to use the suspicious web link and sincere apologies for the negative experience. However, natural curiosity prompted further investigation into this phenomenon, revealing that it was not without reason.
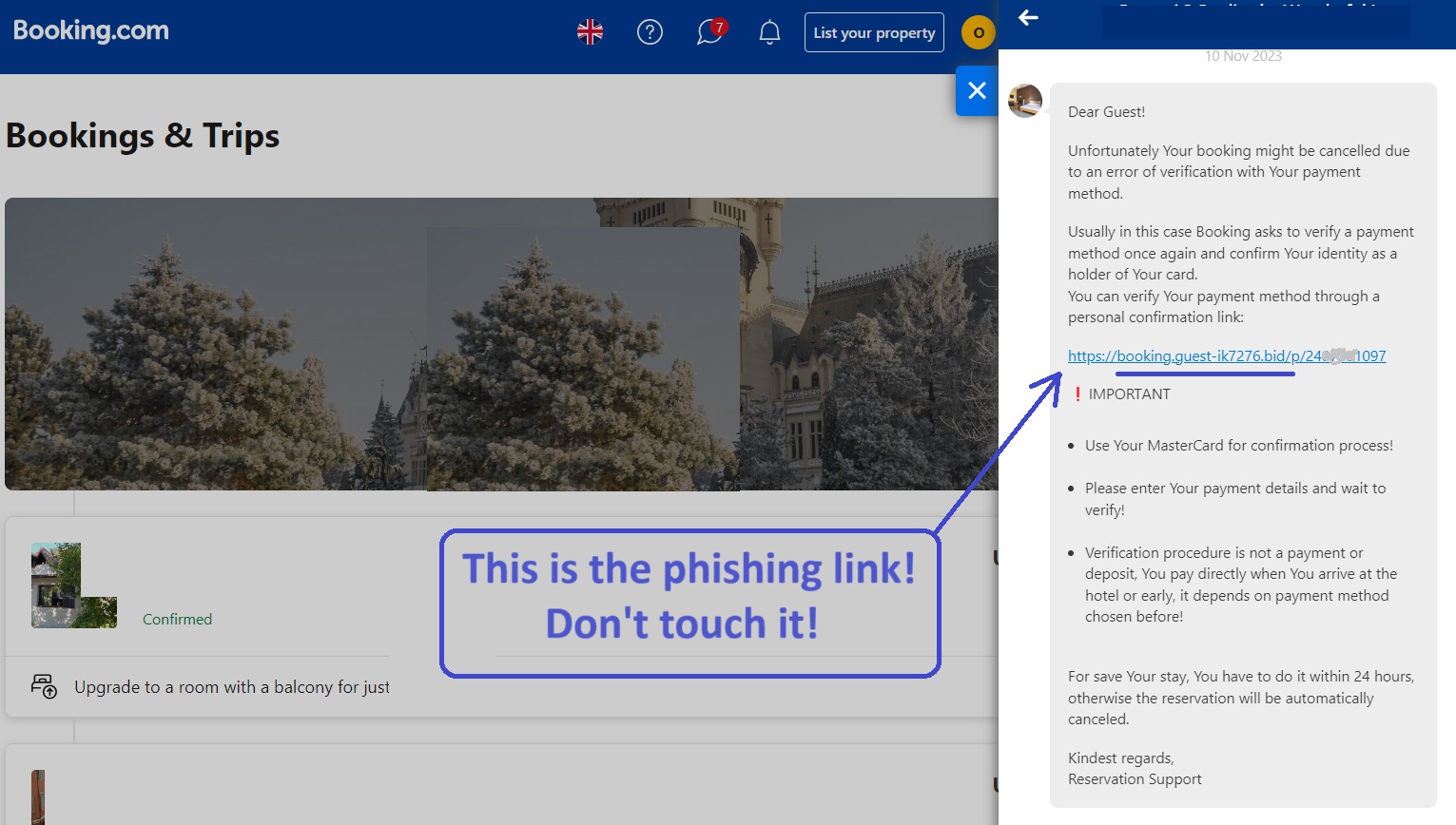 PHOTO: A phishing message looks like this. Pay attention to the web address inside the message. It resembles Booking.com, but it is not. SOURCE: The Gaze
PHOTO: A phishing message looks like this. Pay attention to the web address inside the message. It resembles Booking.com, but it is not. SOURCE: The Gaze
Vulnerabilities Identified: Scammers Exploit Weaknesses in Booking.com System
The situation appears as though scammers have discovered a loophole in the Booking.com system and are taking advantage of it to engage with clients, posing as property owners or administrators.
A massive phishing campaign, identified by the company Perception Point, unfolds in four stages.
In the first stage, perpetrators gain unauthorized access to hotel systems or the account of a specific property owner, essentially taking control of the establishment's Booking.com account. This breach sets the stage for subsequent fraudulent activities.
Moving on to the second stage, after gaining control of the property's account on the booking service, scammers access guests' personal information for hotels or apartments. This data package includes names, booking dates, details about the hotel reservation dates and conditions, as well as payment information.
In the third stage, scammers leverage the stolen data to craft messages aimed at playing on the fears and uncertainties of potential victims. As mentioned earlier, prospective guests are threatened with the cancellation of their bookings within 24 hours unless they promptly provide their credit card details to confirm authenticity.
At the fourth and final stage, scammers compel their victims to visit a phishing page mimicking Booking.com. To enhance the impact on potential victims, this fraudulent page is pre-filled with personal information about them, and the similarity of the web address can be misleading. The disoriented victim then re-enters their credit card information, which the scammers subsequently exploit to obtain funds.
But the primary question remained: how is the takeover of a property account on the booking service? In short, a very convenient yet potentially vulnerable method was used for owners and administrators to access the service. This method allows owners to log in via their Facebook accounts.
Specifically, vulnerabilities identified by Salt Security could potentially impact users logging in through their Facebook accounts. Several security flaws were found in the implementation of the Open Authorization (OAuth) social media login feature used by the Booking.com service.
"Improper OAuth configuration could enable both account takeover (ATO) of customer accounts and compromise the server," reported security researcher Aviad Carmel of Salt Security.
This vulnerability was discovered in the spring of 2023, but since then, there have been at least two powerful waves of phishing attacks via Booking.com, specifically during the summer holidays and now, ahead of the Christmas holidays. Therefore, scammers may be leveraging previously compromised accounts on Booking.com, or they have found new backdoors to achieve their goals. Perhaps, it's both at the same time.
The second version found confirmation in November. This attack seemingly began when a hacker, posing as a traveller, sent emails to various hotels. When a hotel employee clicked on a malicious link in the email, the hotel's computer became infected with a virus. Once the virus was active, it allowed hackers to obtain hotel identifiers and passwords for Booking.com. The rest unfolded according to the familiar pattern described above.
As reported by jdsupra.com, Booking.com recently confirmed the November phishing attack and stated that it is still investigating the causes and consequences. Meanwhile, travellers should not succumb to manipulations about "your booking will be canceled if you don't confirm your details" and avoid phishing links that only appear similar to the genuine ones.